A Look at the Microsoft LAPS Group Policy Settings
The Microsoft Local Administrator Password Solution (LAPS) comes with a Group Policy ADMX template to make configuring it easy. So let’s fire up the Group Policy Management Editor and take a look at the settings.
The settings will be found under Computer Configuration -> Policies -> Administrative Templates -> LAPS.
Lets not waste any further time and just dive straight in.
Do not allow password expiration time longer than required by policy
![]()
If this is not enabled, users with write access to the timestamp property in AD would be able to set that value to any arbitrary date in the future and LAPS wouldn’t complain or reset the password according to schedule. Enabling this setting makes sure that password expiration policy is adhered to.
Enable local admin password management
![]()
The basic on/off switch for LAPS. If this is enabled, then LAPS will manage the Local Administrator account passwords, resetting them to new random passwords when they expire.
Name of administrator account to manage
![]()
If you’ve renamed or replaced the Local Administrator account (which you haven’t if you’ve read our article Local Administrators: To Rename or not to Rename), then you can enable this policy setting to specify the account name to use.
Password Settings
![]()
This is the core of LAPS’ group policy settings, how secure you want the randomly generated passwords to be. The options are:
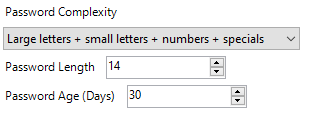
Password Complexity
This defines which letters LAPS is allowed to use when generating a random password. The default (and recommended) is to use uppercase (“large letters”), lowercase (“small letters”), numbers and specials.
Password Length
Specify how long you want the password to be. Given that policy definitions are visible on client devices, I kind of wish Microsoft had given us two separate “Minimum Password Length” and “Maximum Password Length” values here, and when generating a password it randomly selects a value between them. Knowing the password length greatly reduces the time to brute force it.
However, as this isn’t an option, the higher the value the better, while making it too long may lead to confusion and added difficulty when the passwords are needed to be typed in. It can be between 8 and 64 characters, with a default of 14. We normally set this to 25 characters to bring it in line with our own security policy.
Password Age (Days)
This is used to specify how frequently the password should be changed to a new random value. It defaults to 30 days, which should be fine for most purposes. Security conscious teams may want to consider dropping this down though as there is very little overhead to the password reset process itself.
Wish List
That’s all the options you get, and they should be enough to achieve a decently secure Local Administrator policy. However, if I were to get 3 wishes which I, for some reason, wanted to spend on improving the options, what would I add?
Variable Length Passwords
Obviously, there’s the ability for variable length passwords as mentioned above. There isn’t much excuse not to include it, and it really would help lower the risk of brute force attacks.
Custom Character Selection
In place of the “Password Complexity” selection, I’d like to see the ability to specify a list of allowed characters. This would allow you control over which special characters are used so you could go right up into the upper Unicode realms if you wanted, but more importantly it would allow you to easily drop commonly mistaken characters such as the lowercase letter “l” (L), the uppercase letter “I” (i) and the number “1” for example (depending on your font of choice).
Error Reporting
Finally, I’d like to see a more configurable reporting engine, particularly for warnings or errors that may occur during the reset process. At the moment we have the device’s Windows event logs, but it would be great to see some way of output to a custom shared log file, or posting to a given URL so we can perform custom error handling.
What features/options would you add? Tweet us @int64software, we’d be interested to hear.
Conclusion
What is there to say, other than LAPS really couldn’t be easier to set up. This is not a set of policies you’re going to have to have long meetings and longer policy documents on, and bringing it inline with your existing password policies should be a breeze.
Don’t forget to check out our LAPS sister product OverLAPS if you’re looking for a Web UI for LAPS, and Overcee if you’re interested in a more complete device management solution which has inbuilt LAPS support.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd