Free: Windows Privilege Escalation Vulnerability Scan Tool
There exist many actual and potential vulnerabilities in the Windows operating system suite which could leave your systems open to attack. While many of these are patched or mitigated when they are discovered, many still remain as “features” of the operating system.
We’ve isolated four of these vulnerabilities which we feel are the most easily exploitable and written a small scan tool to help identify at risk systems, and are now releasing it for free for anybody to make use of.
Licence
This Windows Privilege Escalation Vulnerability Scan Tool (PEVS) is released under the CC BY-NC-ND 3.0 (Attribution-NonCommercial-NoDerivs) licence  . Meaning that it can be copied and redistributed at will as long as appropriate credit is given, and it is not sold.
. Meaning that it can be copied and redistributed at will as long as appropriate credit is given, and it is not sold.
Vulnerabilities
1. Always Install Elevated
When configuring Group Policy, you may have seen the setting “Always install with elevated privileges” under Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Installer.
If this policy is enabled, it forces the Windows Installer service to always use elevated privileges when running an installation package. Naturally this is incredibly dangerous as it essentially grants administrator rights to any users on the system by crafting a custom MSI which launches a program, or a command prompt, or adds themselves to the Administrators group.
The PEVS tool checks for this by seeing if the policy settings has been applied in the computer’s registry.
2. SysPrep Configuration Files
SysPrep is a tool that comes with Windows and is used when building pre-configured system images for deployment through tools such as Configuration Manager (SCCM). It uses text INF or XML configuration files which specify how the image should deploy to a new machine, and these files could very well contain sensitive information such as usernames and passwords. In most instances, these files are automatically removed when an image is deployed, but we’ve seen reports of them being left behind, along with their tasty contents.
3. Unquoted Service Paths
It’s an accepted quirk (or feature) of the CreateProcess WinAPI function that unquoted executable paths are parsed left to right, and if you path contains a space, matches in parent directories will take priority over your full path.
What does this mean? Consider the path “C:\Program Files (x86)\My Program\myprogram.exe“. Without the quotes, CreateProcess will search for executables in the following order:
1. C:\Program.exe
2. C:\Program Files.exe
3. C:\Program Files (x86)\My.exe
4. C:\Program Files (x86)\My Program\myprogram.exe
So you see, in this case a user has the opportunity (if they possess the permission to create files there) to inject executables at 3 points which would be run instead of your program.
This is particularly a problem with Windows Services, because services often run as System and therefore have the highest assignable permissions on the computer, and because the Windows uses CreateProcess to launch services.
For this reason, PEVS includes a scan to check all services (excluding those located in C:\Windows\System32 and C:\Windows\SysWOW64) to make sure that their ImagePath properties have quotes.
4. Service Registry Permissions
Finally, the other way to hijack a Windows Service is to simple modify the registry entry for it to point its ImagePath at another executable of your choice. Of course that portion of the registry usually requires Administrator rights to modify, but we have seen systems configured to all members of the Users group, or indeed the Everyone object, to have write access for some reason. Sometimes this is a mistake of a system administrator, other times its poorly configured third party software making the change.
Either way, PEVS will check all services to make sure that they are properly quoted.
Does it make any changes?
No. PEVS is not a remediation tool, it is simply a scanner to check for potential vulnerabilities that you may want to look into.
Usage
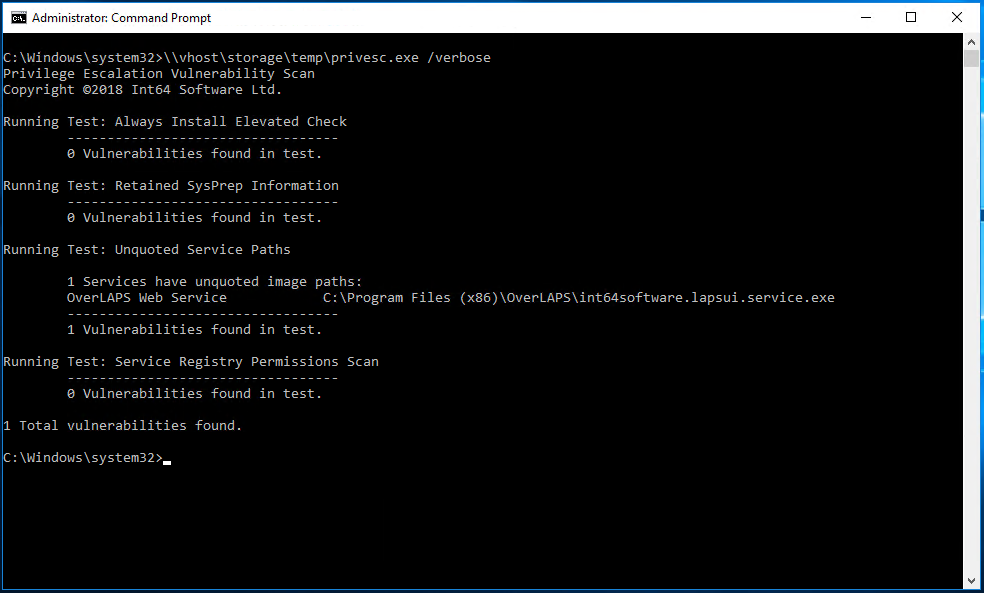
Extract the files to somewhere easily accessible and launch a command prompt as Administrator. Note that if you want to scan remote devices, you’ll need administrator rights to them as well.
privesc.exe [hostname] [/verbose] [/pause]
[hostname] – (Optional) name of the computer to scan.
[/verbose] – (Optional) show additional information.
[/pause] – (Optional) Require user input before closing.
Return Codes
If a vulnerability is detected by one of the scans, the return code of the application will be that of the last one found.
100 – Unquoted Service Paths
300 – Service Registry Permissions
400 – Always Install Elevated
500 – SysPrep Configuration Files
So if an unquoted service path vulnerability is found and Always Install Elevated is enabled, then the return code will be 400. You can also examine the tools output for a full breakdown of its results.
Overcee
PEVS will work perfectly well as a defined Remote Execute tool, just set it to run without any parameters and Overcee will manage the capture of the return code and output for further analysis later.
Download
Click the link below to download PEVS.
Privilege Escalation Vulnerability Scan Tool 1.0 (17kb)
Support / Warranty
Please read the included EULA prior to using PEVS. If you disagree with any of the content of this, then please delete PEVS and do not use it. PEVS is provided as-is, but if you experience any problems then please contact support@int64software.com for assistance.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd