OVERLAPS for Microsoft LAPS Update 2.0.0
Our hugely popular web interface for Microsoft’s Local Administrator Password Solution (LAPS) has had a massive update which is now available from the OVERLAPS website.
From fundamental changes to the core systems of OVERLAPS, to a host of new features, this marks the largest update that we have ever released.
Below we’ll take a look at some of the more significant new features one-by-one. Settle in for a lengthy read folks!
Features
New Database Backend

As an inevitable result of OVERLAPS’s popularity, we’ve seen it being used on a huge variety of domain environments. Many of these are of a size that we couldn’t have predicted, or use complex configurations that push Active Directory to its limits. So we’ve come to realise that OVERLAPS would really benefit from a database backend, both in terms of storage efficiency and overall performance.
Because we don’t want to burden our clients with the additional overhead (not to mention cost) of SQL Server, we’re opted to implement SQLite for the majority of OVERLAPS’s data storage. This has not only brought the aforementioned benefits of improved storage and performance, but allows us to bring you new quality of life features such as the ability to filter the history log.
Don’t worry about losing your current settings or data though, as we’ve put together a utility to handle the migration of your existing data to the new database which runs during the update process.
Phonetic Alphabet Password Display
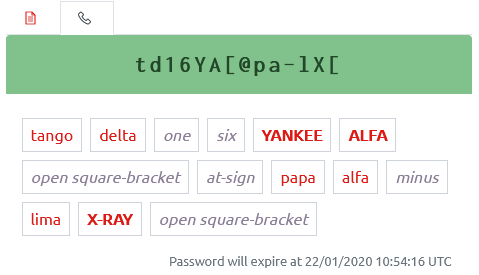
At the request of our customers, we have added a selection of phonetic alphabets to OVERLAPS. When viewing a computer’s password, you can now switch to this view which will make it much easier if your Service Desk team need to read the password out over the telephone.
Included by default are two variations of the NATO phonetic alphabet, as well as some language-specific alternatives. But don’t worry if you can’t find one that fits your needs as we’ve made it easy to modify them or create your own (see section 8.3.5 of the updated Setup Guide for more information).
Two Factor Authentication (2FA)
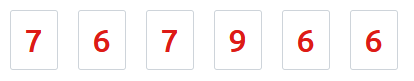
To improve security, OVERLAPS now supports the use of Google Authenticator to provide Two Factor Authentication. When enabled in a user’s profile, this system allows them to use an authenticator app on their smartphone to generate a unique One-Time Password (OTP) which will be needed during login.
This means that knowledge of a users username and password will no longer be sufficient to gain access to OVERLAPS if they have 2FA enabled on their account.
Authorisation Request System
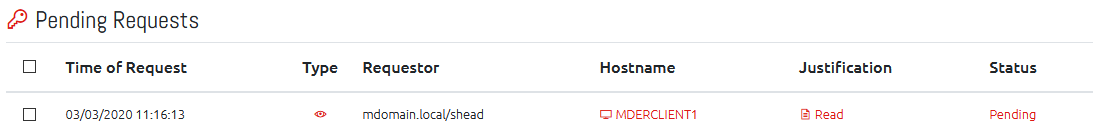
Instead of giving users immediate access to computer passwords, you can now have users that require authorisation before they can read and/or expire a LAPS managed Local Administrator password through OVERLAPS.
The process for viewing passwords goes like this:
- A user clicks on a computer to view its Local Administrator password
- Instead of displaying the password, OVERLAPS now prompts them to provide justification and submit their request.
- Named Authorisors for that computer’s Organizational Unit are emailed to notify them that they have Authorisation Requests that require their attention.
- The Authorisor can either Allow or Deny the request, optionally providing feedback or guidance if needed.
- The original requestor is emailed to let them know that their request has been updated.
- If the request was authorised, then they can now view that computer’s local admin password.
And expiring/resetting passwords works in much the same way.
By default, once authorisation is given and the requestor views that computer’s password, the request is immediately expired so that subsequent attempts to view the password will require another request. However, you can specify a grace period (in minutes) after their initial view that the user can continue to view the password through the Config screen.
Note that the Authorisation Request system requires the Email System to be configured (see below) so that notification emails can be sent out.
Notification System
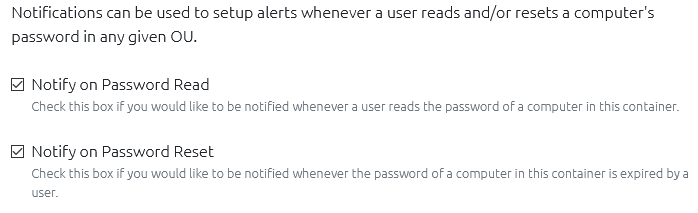
If you’ve configured an email server for OVERLAPS to use, users will now be able to setup notifications for when anyone reads or expires a computer’s password in a particular Organizational Unit.
This is primarily aimed at admins who want to keep an eye on sensitive systems, but can be used by any OVERLAPS users for any purpose they see fit.
To prevent spamming users who opt to use this service, notification emails are grouped and only sent out periodically. This is configurable when setting up the notification.
Email Sending Capability
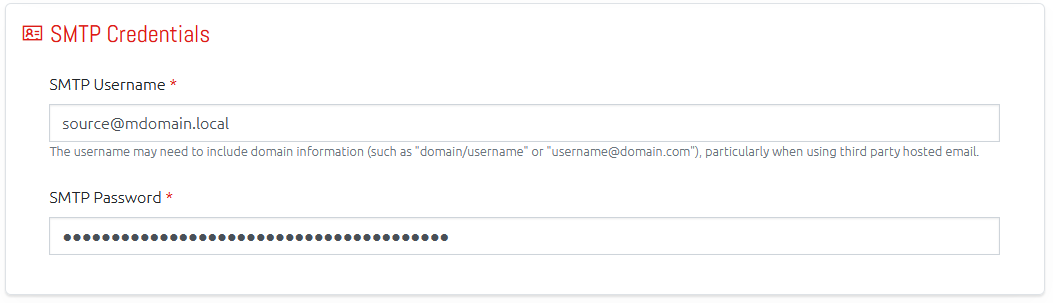
OVERLAPS can now be given the details of an SMTP email server entered which it will use to send emails to system users. This must be configured in order for the Authorisation Request and Notification systems to work as they both require the ability to email users.
Don’t worry if you don’t have a compatible SMTP server, we also support the use of “Pickup Drop Folders” or “Pickup Directories” for systems that support it such as in IIS. These more specialised systems offer the ability to support much more complex email delivery systems.
Note that the SMTP credentials, if entered, are stored encrypted on the server.
Per-Container Permissions
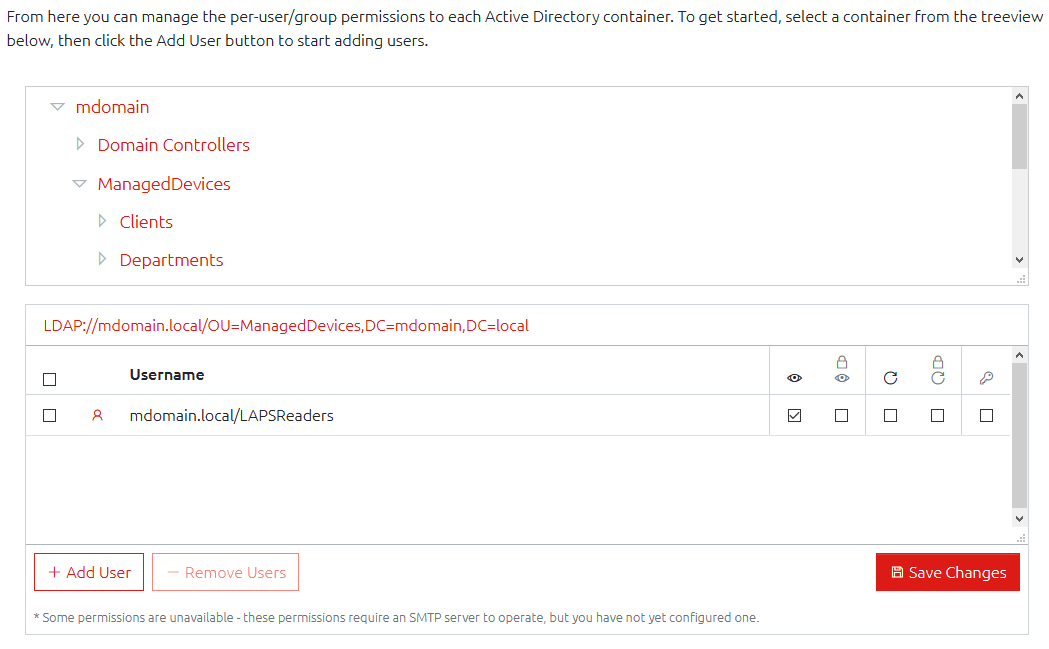
Previously, permissions were handled in a “Per-User” way, adding each Active Directory container to the user or group’s account to say that they could access the computers in that container.
We’ve completely re-written this to use a more easily configurable “Per-Container” permissions system. This works more like what you would expect in a Windows filesystem, or Active Directory itself, where each container now has users/groups and permissions applied to it.
While the distinction may seems minor, this is a much more intuitive and easy-to-use system, and it makes managing OVERLAPS a lot simpler. This also allows us to split the Read and Expire permissions into distinct options so that you have greater control over your users.
No More Root Container Requirement
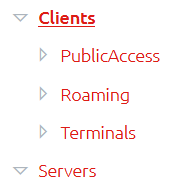
In previous versions of OVERLAPS, all users had to have access to a full branch of the Active Directory tree, from the very top level (root) all the way down to the sub-container that they actually need access to.
For example, if you had a domain “Root” with container “Folder-A” in it, in order to have access to “Folder-A” a user would also need access to “Root” and any containers in between them.
This is no longer the case. If you need to give access to “Folder-A” now, you need only give access to that container. OVERLAPS will ignore/deny access to any other containers that the user doesn’t have permission to.
More Historical Information for Auditing
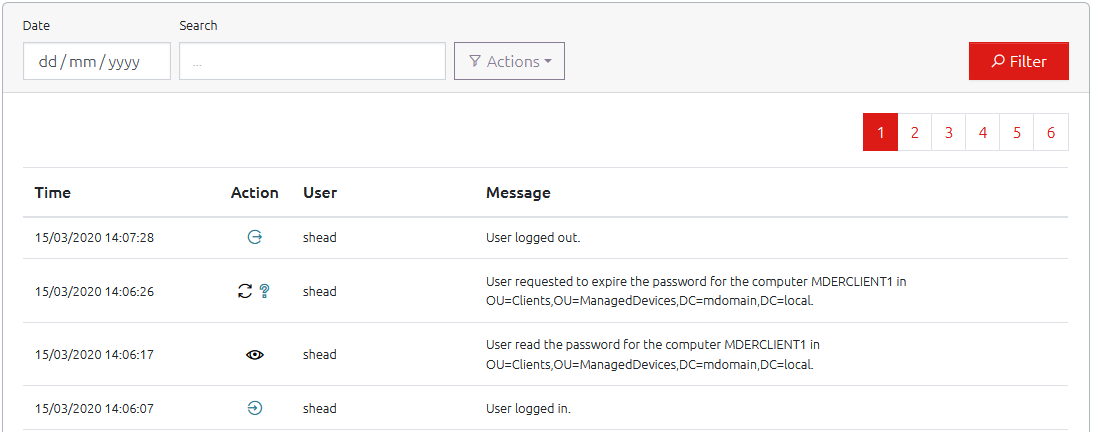
We’ve greatly increased the amount of auditable information that is logged in the History Log in OVERLAPS to allow you to monitor its use even more closely. Whereas we just used to log computer password reads and resets, now you’ll have information on users logging in and out, Authorisation Requests being dealt with, and more.
In addition to this, the history is now fully searchable and filterable to make identifying particular users, computers or events much simpler.
HTTPS Redirection

Previously we recommended that once you have enabled your HTTPS encrypted connection to OVERLAPS you should disable the unencrypted HTTP connection.
In order to align more closely with security best-practice this is no longer the case, instead we now recommend leaving HTTP enabled as OVERLAPS will automatically redirect users to the secured HTTPS connection instead.
Separate Active Directory Credentials
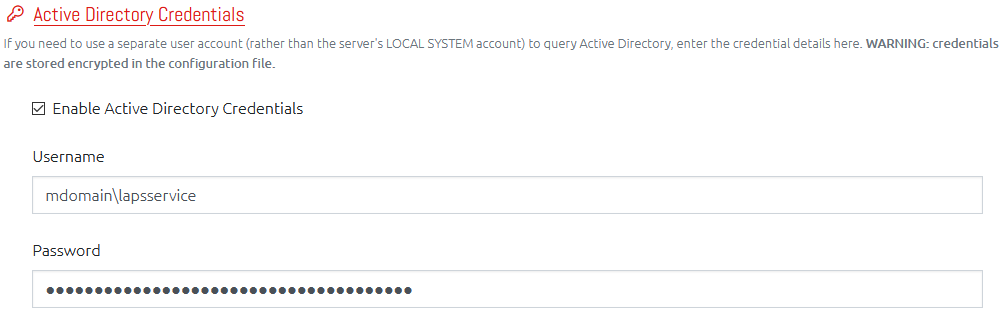
This was previously a feature which could only be enabled with some modifications to the OVERLAPS ini file. It grants the ability to specify separate credentials that OVERLAPS would use to query LAPS properties in Active Directory.
The feature has been modified slightly so that OVERLAPS will now use the credentials for all queries to Active Directory, and it is now configurable from within OVERLAPS and not hidden away.
The credentials are stored encrypted on the server.
IP Address Binding
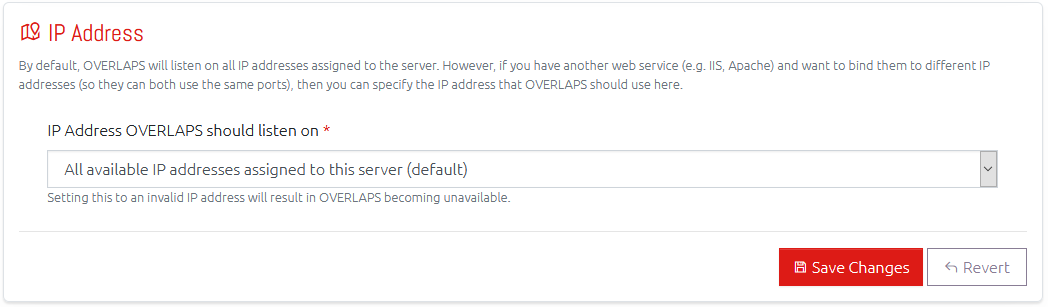
For environments which have other web hosting solutions on the same server (e.g. IIS, Apache), but where changing the port number that OVERLAPS is hosted on to an unused port is not desirable.
By default, OVERLAPS will bind to (listen on) all available IP addresses. However, if you have multiple network adapters in the server, or multiple IP addresses assigned to one network adapter, it is now possible to tell OVERLAPS to bind to a particular IP address. Doing the same with the other application will then allow both to use the same port but on different IP addresses.
Initial Work on Multi-Language Support

We’re incredibly proud of the number of different countries we have customers in now, so we are now prioritising work on multi-language support.
To this end, this version includes the framework which will allow us to start adding more languages to OVERLAPS in the future. Note that it doesn’t actually include anything other than English yet, but watch this space.
We’re not yet sure if these will trickle out one language at a time in future patches or if we’ll get a few done and release one “language pack”, but once we’ve decided the best course of action we’ll let you know.
Remember your Last Container
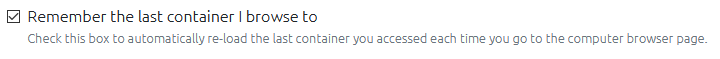
OVERLAPS will now (by default) remember the last container (Organizational Unit) you visited and automatically return you to it. This makes pausing and resuming work, or repeating work on the same computer much simpler.
If you don’t like this feature though, you can turn it off in your Profile.
Easier Access to Child Containers
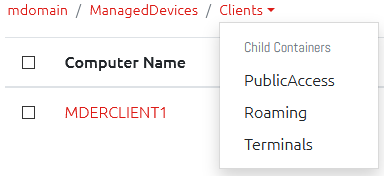
We’ve added a simple dropdown to the end of the current container’s breadcrumb list for any containers sitting immediately below it in the Active Directory tree. This is just another quick Quality of Life improvement that can save you a few seconds here or there.
A New Unified Config Tool
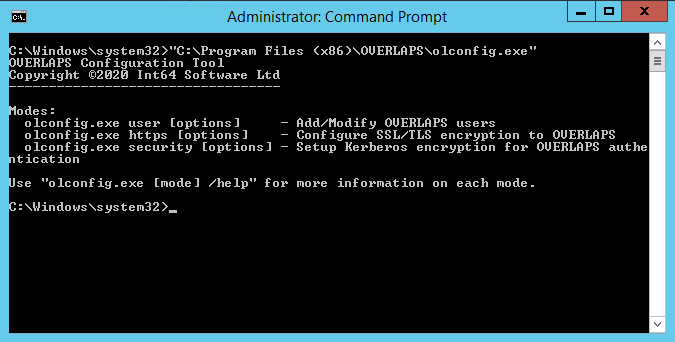
We previously had a command line tool (“lapsuser.exe”) which could be used to add your initial administrators so that you could login and really start to work with OVERLAPS.
We have now retired that single-purpose tool and replaced it with “olconfig.exe”.
OLConfig can do everything that the old tool did and more. In a bid to simplify the initial setup process, we have now added the ability to install and setup SSL/TLS certificates for HTTPS, and functionality for configuring Kerberos support.
For more information, see the updated Setup Guide.
And more…
These are the major features you can look forward to in this update, but for each major feature there are many minor tweaks and fixes throughout OVERLAPS.
Being the culmination of 4 months of hard work, this is easily the biggest update we’ve released yet, and we hope you’ll love it.
Updating to OVERLAPS 2.0
We simplified our installer setup a few updates ago, so now its just a case of downloading the MSI from your Downloads page and running it on the OVERLAPS server.
As this is a major upgrade which makes significant changes to your config file, we make sure to backup your current file to a subfolder in the same location called “dbmbackup”. This makes restoring it if an issue is discovered really simple.
Remember to pickup the version 2.0 Setup Guide from your Downloads page while you’re there as we’ve fully updated it with the latest information as well.
Update 2.0.1.0 – 31st March 2020
We’ve released another minor update to fix a small issue described by one of our customers, and to fix a couple of minor things that have come up through our own testing since 2.0 was released.
Note that you don’t need to install 2.0.0.0 before installing 2.0.1.0, you can intead go straight to the latest version.
Getting Support
This is a very large update which includes many core changes to almost every level of our codebase. While we’ve done our absolute best to make sure it is bug free, there may be one or two unavoidable teething issues to start with.
If you work in a high profile or key industry where even a little bit of disruption can have huge knock-on effects, it may be worth holding off for a couple of weeks to allow us to iron out any remaining glitches.
Otherwise, if you do encounter any problems, we apologise for any inconvenience that may be caused. Please let us know with as much detail as possible what problems you’re having and we’ll do our best to resolve them for you.
Alternatively, you can contact us on Twitter at @Int64Software
Purchasing OVERLAPS
If you’ve been waiting to join the ranks of OVERLAPS users then there has never been a better time. Just go over to the product page and check it out.
If you’re looking for a reseller rather than ordering directly, we’ve been working with both SoftwareONE and SHI, so feel free to contact them and ask about purchasing OVERLAPS.
Alternatively, if you have another preferred reseller, ask them to get in touch with us (using the Contact Us page linked above) and we’ll do everything in our power to help.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd