
OVERLAPS for Microsoft LAPS Version 3.0
Today we will be releasing update 3.0.0.0 of OVERLAPS, our popular web interface for controlling Microsoft LAPS managed Local Administrator passwords. Below we’ll highlight the biggest changes coming with this version, or scroll to the bottom for the full change notes.
Main Features
Computer Management
We’ve added a new computer management system, starting with two simple tools: Ping and Group Policy Update.
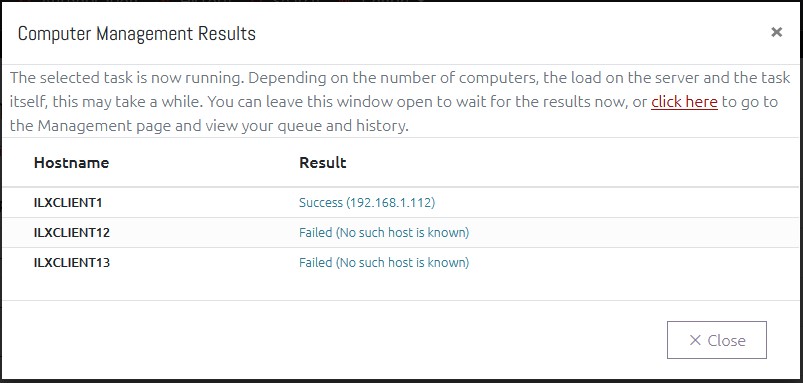
Since expiring a password in OVERLAPS doesn’t actually cause the computer to change its password, we wanted to provide a way to force this by granting the ability to trigger a remote Group Policy update. However, since we have other ideas to make OVERLAPS even more effective, we decided to implement this as a Computer Management engine within OVERLAPS.
To start with only two tools are included: an ICMP Ping for checking whether a in-network computer is online or not (and getting its IP address), and a Group Policy update tool which utilises WMI to trigger the update on a remote computer (this requires WMI to be enabled and configured to allow the OVERLAPS server permission to run this task).
Additional Languages
After adding the option for US English in OVERLAPS recently, we have now added an additional 4 languages: French (fr-FR), German (de-DE), Italian (it-IT) and Spanish (es-ES).
Note that these are machine translations provided by DeepL, so we do expect there to be one or two minor mistranslations. Please report any such mistakes to us (support@int64software.com) and we will correct them.
Additional Notification Recipients
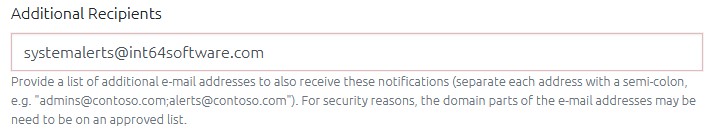
You can now enter additional email addresses when creating Notifications (for when passwords are read or expired).
For security reasons, the domain of these email addresses can be limited from the Configuration page.
And more…
Continue reading for the full list of changes in this release, or head over to the Downloads page to access the update.
Full Change Notes
Computer List and Passwords
- Added the ability to specify expiry date/time when expiring passwords. This can either be enabled globally for all users with the Expire Passwords permission or per-user via their User Access Levels. This cannot currently be enabled for users who need to submit Access Requests to expire passwords though.
- Added a computer information modal for viewing additional information about a computer’s Active Directory properties. A new per-container permission has been added to allow users to view this.
- Added the ability to edit the description of a computer object in Active Directory. The OVERLAPS server must have the “Write Description” permission in AD. A new per-container permission has been added for this ability.
- Added the ability to enter one or more alternative email addresses when creating a notification (so it can go to a distribution group for example). By default, to prevent abuse, the addresses are limited to known domains (current domain, other domains in the forest, and domains in other trusted forests), this can be configured from the Email Settings page.
- Added the computer control buttons (bottom of the computer list) to the top of the page as well for easier access.
- Fixed issues with the computer select checkboxes not working for some search results.
- Reworked computer search feature to resolve an issue with the sorting mechanic.
- Updated container permissions so that anyone with a valid permission to a container can now view the computers in that container. So users don’t need permission to read computer passwords if they just need access to the computer’s information, or to run a ping on it.
- Added missing notification when a Authorisation Request for a computer password reset is authorised.
Computer Management
- Added Computer Management capability including separate per-container permissions and Management page for viewing the results of your recent Management tasks. Each tool must be manually enabled from the Site Settings page.
- Added a Computer Management task to ping computers from OVERLAPS
- Added a Computer Management task to run a remote Group Policy update on computers from OVERLAPS. This requires WMI to be configured on clients and the OVERLAPS server to have permission to use it (see the Administrator’s Guide for more information).
User Management
- Added a tool for bulk importing Self Service users and their computers from a CSV file.
- Add ability to enforce Two Factor Authentication, when enabled users will be prompted to scan a QR code and then enter the code from their authenticator app before they can proceed.
- Changed the LDAP and Directory Searcher so that when searching for a new domain user to add to OVERLAPS they will now also search by Display Name as well as the sAMAccountName as was the previous behaviour. To avoid creating duplicate queries, the Principal search has not currently been updated to do the same.
- Changed Add User handling so that if the auto-suggest is unable to find the user in Active Directory, it will now attempt to use the entered username to find the user instead.
Self Service
- Added Authorisation System to Self Service users, now each computer can be tagged to require a nominated authorisor for that AD container to authorise a request before the user can access the password. A new permission “Authorise Self Service” has been added to accommodate this.
- Applied Rate Limits to Self Service users
- Fixed an issue when saving the Self Service settings for a user without adding any computers (just setting the Managed By property).
- Fixed an issue where Self Service users may still have seen the “Browser” button in their menu, which would then show an error if used because they don’t have permission to access any containers.
User Profile
- Added a list of notifications the current user is subscribed to to the Profile page with ability to remove them.
Language
- Added German, French, Spanish and Italian machine translations (provided by DeepL). More languages to follow.
Configuration
- Fixed a bug when saving Auto Reset values which was failing the valid values validation process.
- Added the ability to search the configuration file in the Configuration Utility
- Added the ability to unbind certificates from the Configuration Utilty when there is one already bound to the selected hostname / IP address
- Added certificate store option to Configuration Utility to fix a problem where official third-party certificates (e.g. Thawte, LetsEncrypt, etc) need importing into Trusted Root Certification Authorities whereas Self Signed certificates need to go into the Personal store.
- Added the ability to give Organizational Units an alternative Display Name. This allows you to give containers friendlier designations for end users.
- Fixed an issue where it wasn’t possible to grant group members permissions to containers individually.
System
- Unified page handling for login and two-factor authentication entry pages
- Changed default behaviour so that the webhost will failover to a wildcard binding in rare cases where no IP addresses can be found on the server. As this presents a possible surface of attack, administrators will receive a warning about this on the Host settings screen advising them to set the IP address manually.
- Fixed a main menu display issue on small screen devices
- Added the LAPS Active Directory Checker tool (“lapscheck.exe”) for scanning a particular OU or computer object to test their LAPS relevant permissions and access to the LAPS properties. This can be passed a username and password for checking different accounts, or use the “lapscheck_system.exe” tool to run it as NT AUTHORITY\SYSTEM to simulate OVERLAPS’s default setup. See lapscheck.readme.txt for more information.
- Added support for LDAP and Security Principals for computer operations (on top of existing Directory Searcher) for increased compatibility across environments.
- Changed user authentication over to using the defined primary/fallback methods as used by other user queries
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd