16. Reports
The Reports page is used for hosting dynamic lookup data to identify problems or areas for investigation. You can select the report that is displayed by clicking the Report name link, and you can change which OU is being scanned by clicking the Domain/Container link.
Note that in order to view Reports, it must be enabled in a user's User Access Levels, see Changing User Access Levels for more information.
Currently there are two reports available:
16.1 Computers with an Expired LAPS Password
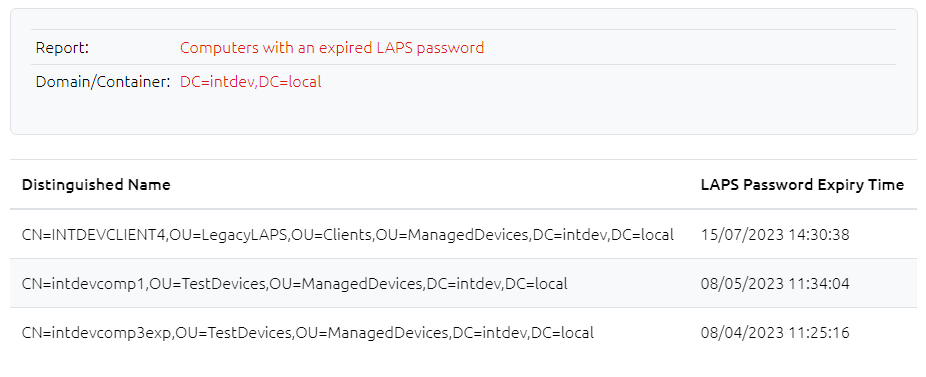
This report shows any computer where the LAPS password's expiration time has been exceeded, meaning that it is due to be reset. Due to the way LAPS works, it may be normal to see some computers appearing in this list from time to time, but if the expiry time shown is considerably old then it may be worth investigating.
16.2 Computers without a LAPS Password
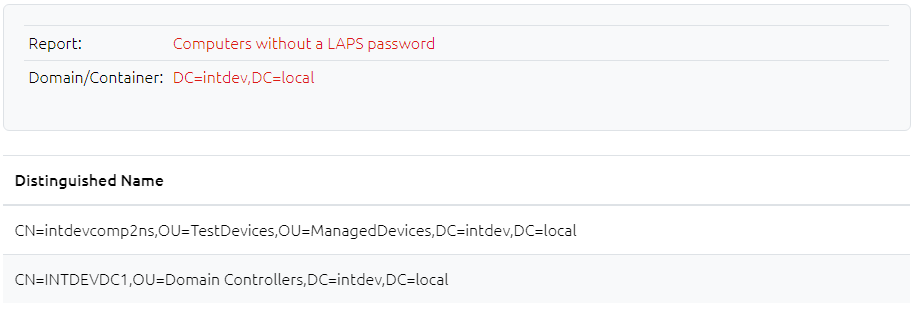
Shows a list of computers who do not have a LAPS password attribute set (either legacy ms-Mcs-AdmPwd, new unencrypted msLAPS-Password, or new encrypted msLAPS-EncryptedPassword). If the computers have only recently been domain joined then this may be normal, but for older devices this may indicate they are having problems processing their group policies.
16.3 Password History
This report lists all devices that the current user has Read Password permission to and allows them to view a complete password history for them. If they also have the "Allow Viewing the Password of Deleted Devices" setting set to "Allowed", then this will also permit them to view the passwords of devices which have been deleted from Active Directory.
16.4 Authorisation Request System Events
This report lists all Authorisation Request System events that have occurred, showing the date/time of the event, and the user who submitted the request. This report is useful for auditing and tracking authorisation requests and reponses.
16.5 Justifications Given for Reading Passwords
Reports all justifications that have been provided by users when reading passwords.