Tutorial: Privilege Escalation Vulnerability Scan Tool and Overcee
We previously mentioned that the free Privilege Escalation Vulnerability Scan (PEVS) Tool released last week could be perfectly combined with our Delegated Device Managements platform, Overcee. So we thought we’d delve in and show you how this simple task can be setup.

Sharing Tools for Execution
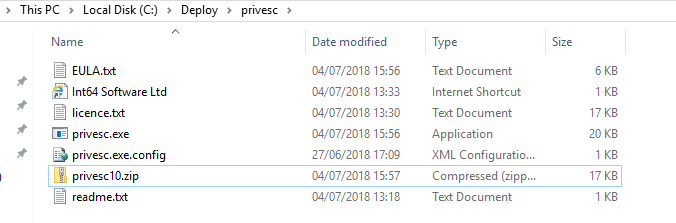
In our development environment, we already have a shared folder configured for deploying various tools and installers across the network. Its NTFS permissions are simple as the Remote Execution tool run as Local System on our client devices.
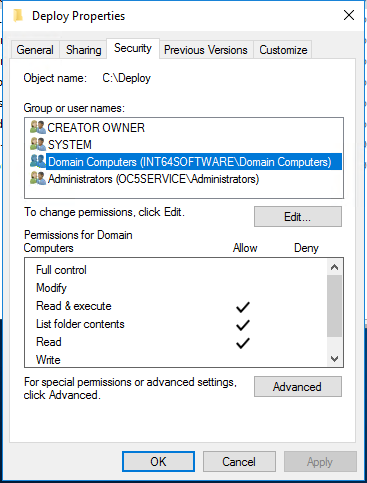
Here we’ve just added the Domain Computers and granted it Read & execute permissions.
Now we just need to copy the PEVS files into it.
Configuring the Overcee Tool
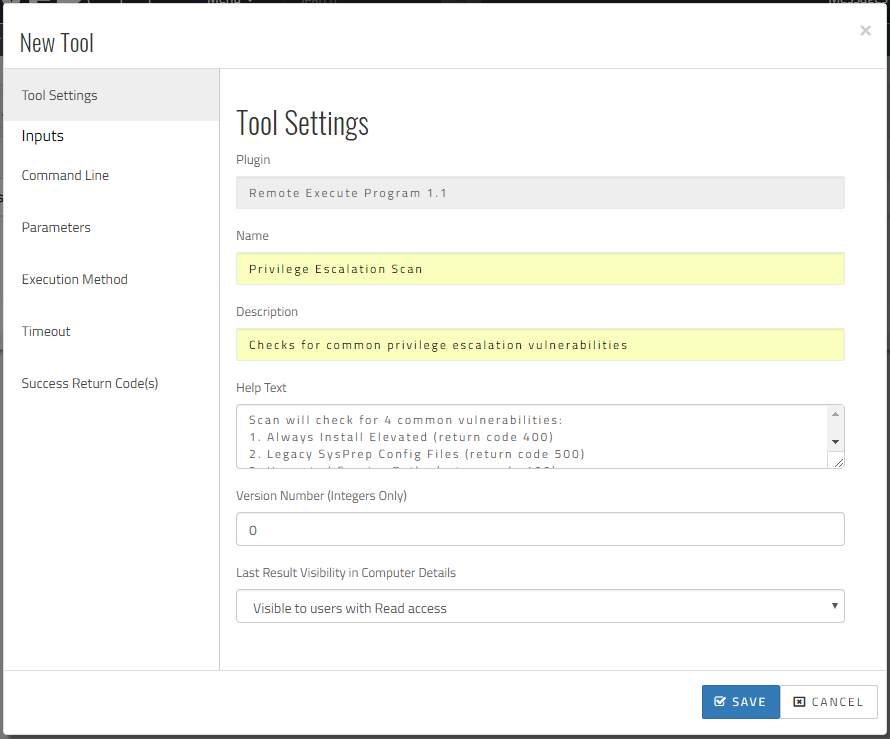
That done, we can head straight into Overcee and create a new Remote Execution tool to run PEVS.
We’ve been over the creation and configuration of tools in previous blog posts, as well as having extensive information in the Overcee documentation, so we won’t go over the all of the options here.
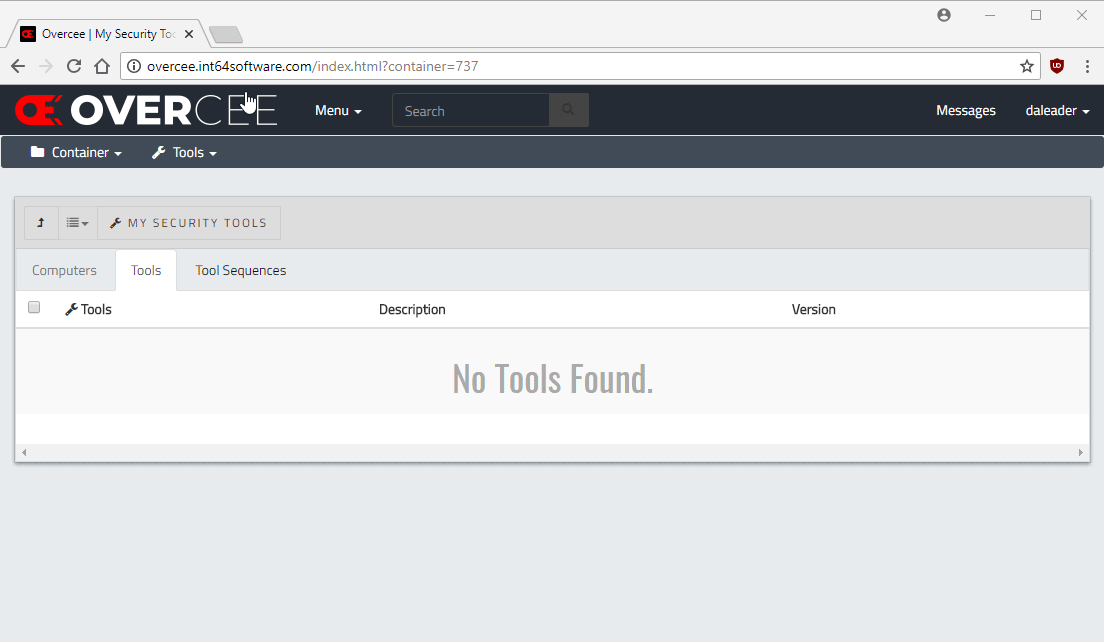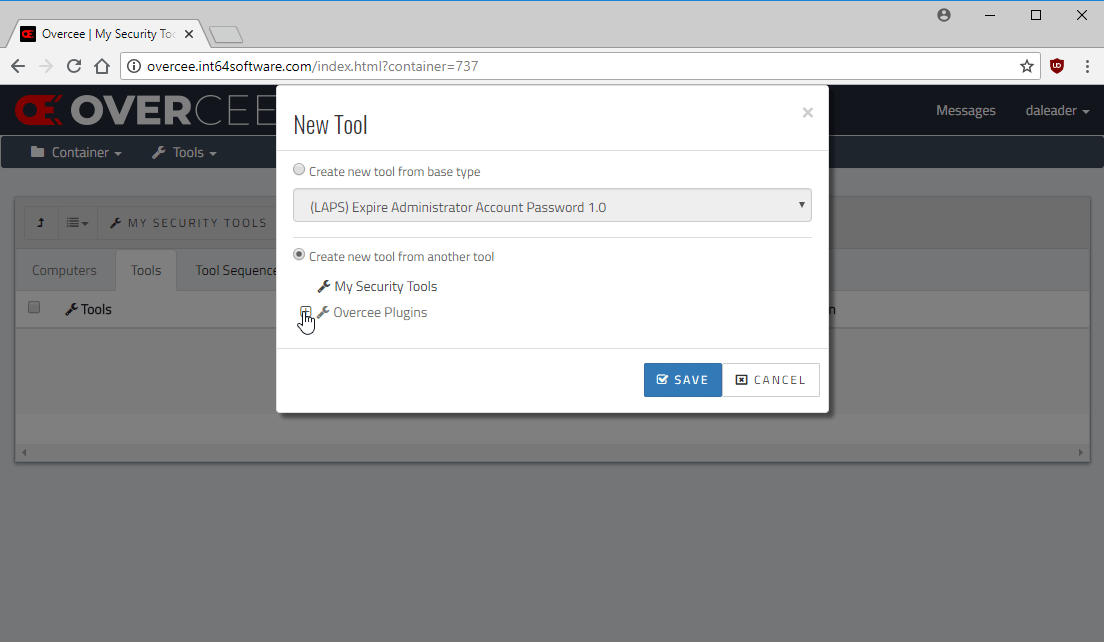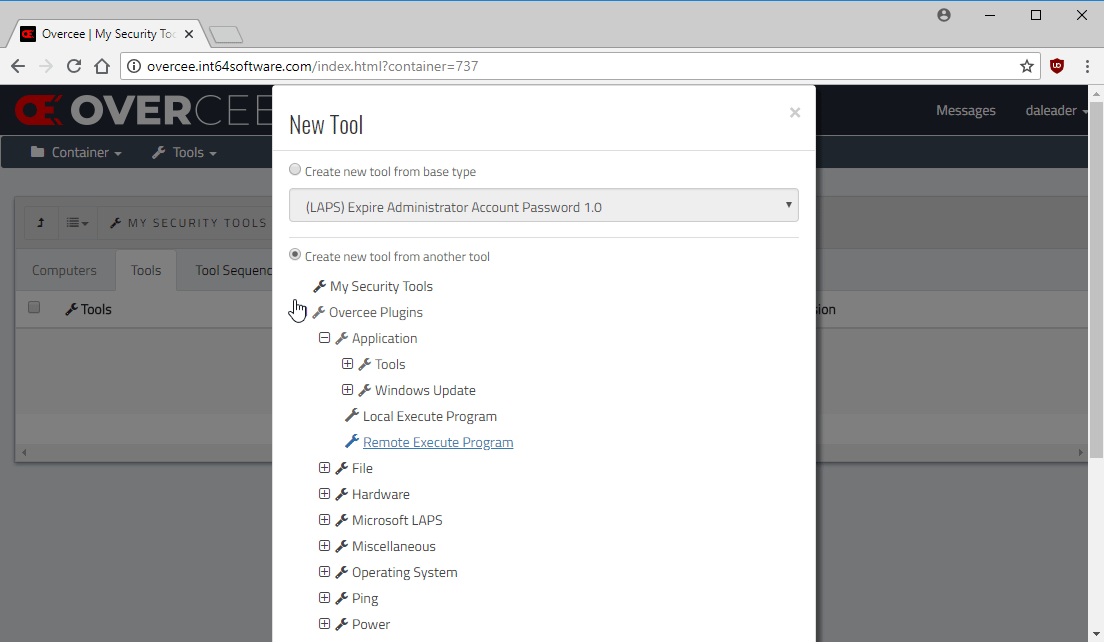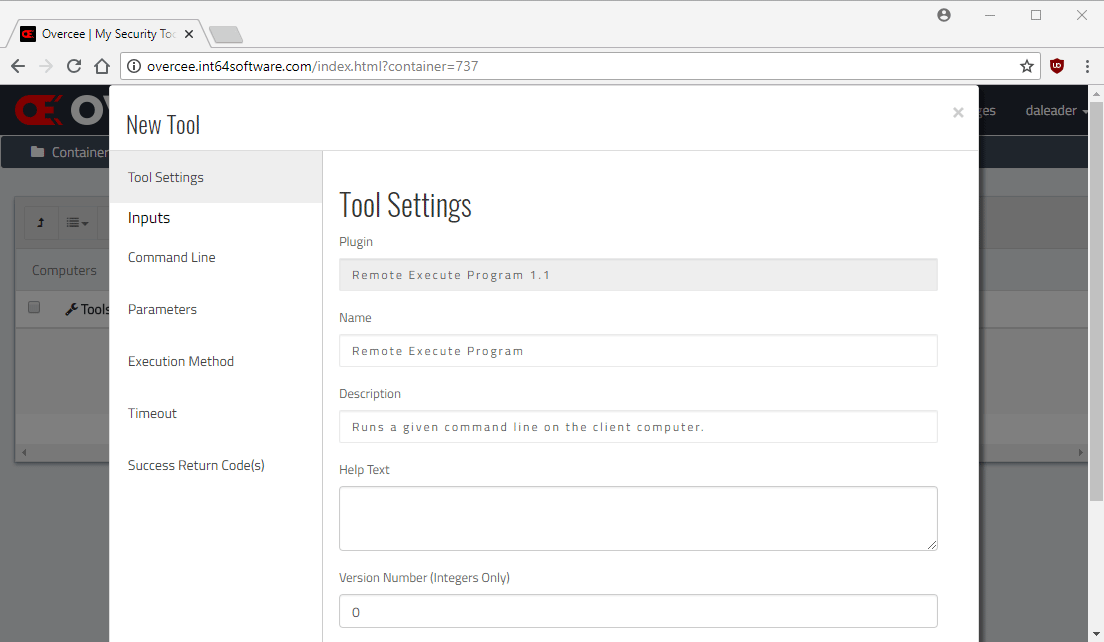
Here we’ve set the new tools name, description and help text to relevant values to help identify the tool and what it does.
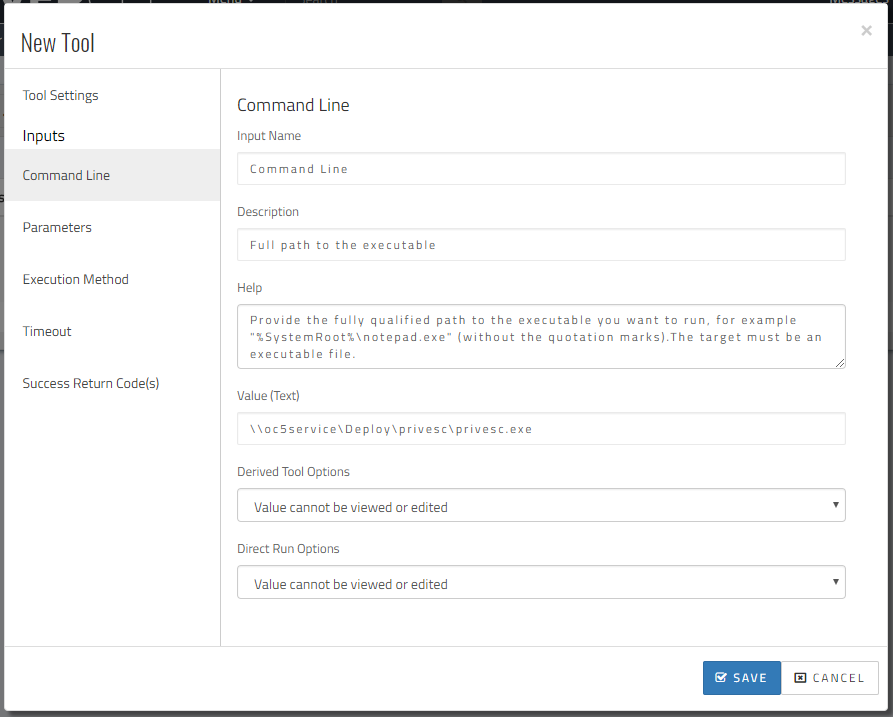
The Command Line is the most important section for us here as we point it to our development server’s “Deploy” shared folder and the privesc.exe PEVS executable.
By default, PEVS doesn’t require any command line options when it’s running locally on the remote computer (i.e. through the Remote Execution tool).
Note that we lock down the tool completely so that future tools derived from this one, and when this tool itself is run, none of the variables can be modified (unless the user has write access to this tool). For more information on this, see our article on Understanding Overcee Permissions.
Conclusion
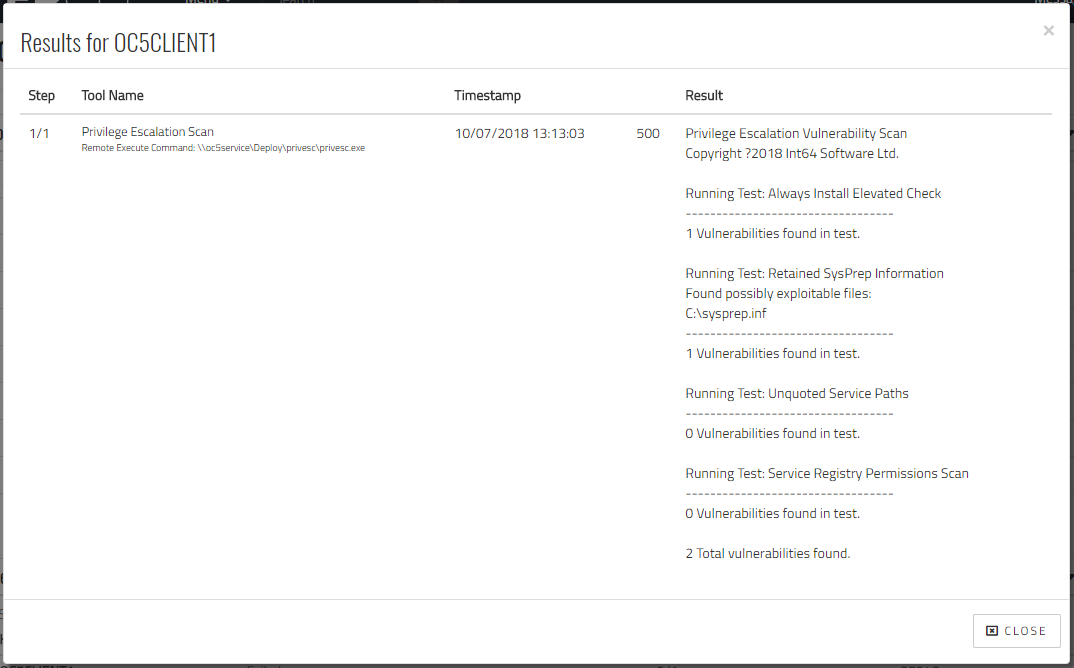
That’s it, with the tool created, we are now free to run it on our client devices.
Here you can see the result of running it on a device which has a couple of (deliberately placed) vulnerabilities.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd