
Why aren’t you using Microsoft’s Local Administrator Password Solution (LAPS) yet?
We sysadmins have many concerns over security. Whether you manage 100 or 10,000 devices, effectively securing your devices will lead you down the same routes of discussion. You’ve deployed a respected antivirus solution, locked down Group Policy, and monitor for the slightest indication that you may be under attack. However, breaches still occur. Today we’re going to look at one of the frequent targets of these attacks: the Windows Local Administrator account.
Standard Operating Procedure is to disable the account, but they find ways to re-enable it, so you need to make sure it has a secure, non-recurring and frequently updated password. So what options do you have?
Options for Securing the Local Administrator Account
The first option is one you should never adopt: setting the admin password to the same thing on all devices. This turns every device into a possible attack vector, and opens your network up to lateral attacks. The attacker can now gain admin rights to every Windows device.
The second option to avoid is one I’ve seen (and been forced to implement) in multiple places: the formulaic approach. By taking some value unique to each device and combining or encoding it with date values and nonce data to produce a different, but predictable password for each device. What’s wrong with this approach?
- Your formula must be simple enough to calculate by hand, because your Service Desk team are going to need to use it in the field.
- People who know the formula may leave your company, and take the knowledge with them.
- If just one password on one device is brute-forced, it would an easy process to reverse engineer its formula.
One way or another someone undesirable could learn the formula, and that’s a bad thing, because now they have Administrator access to all of your devices.
The third, and final option provides a solid solution to all of the problems with the previous options: Microsoft LAPS (Local Administrator Password Solution) [download version 6.2 here].
The Microsoft LAPS Solution
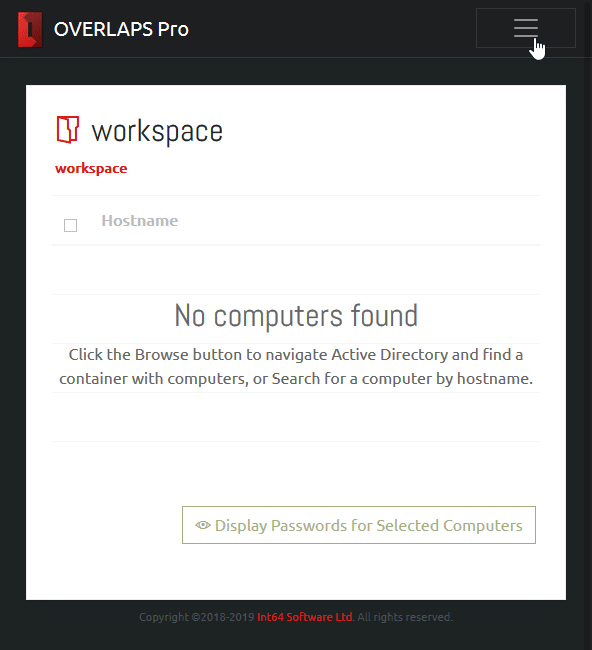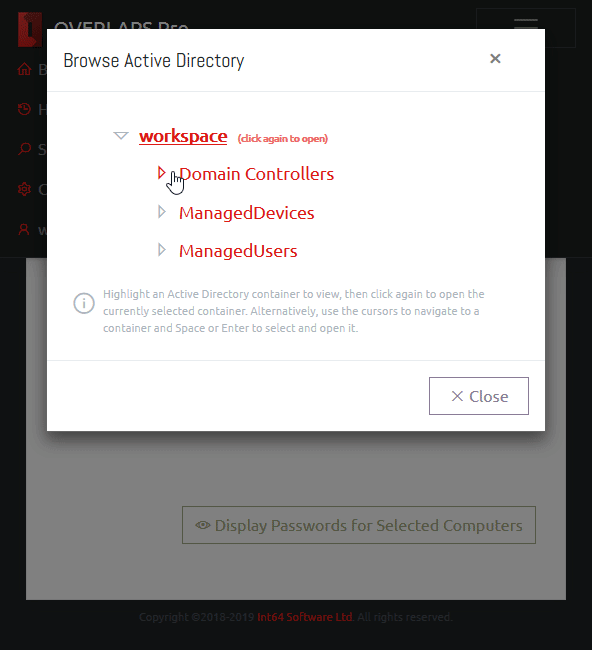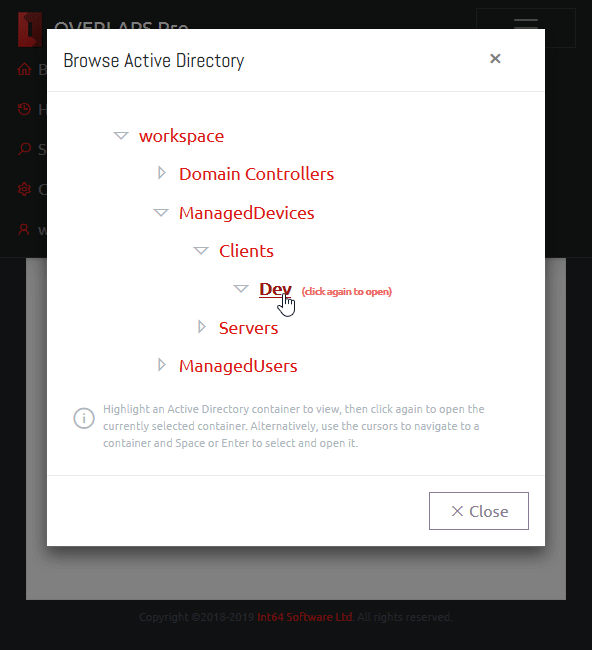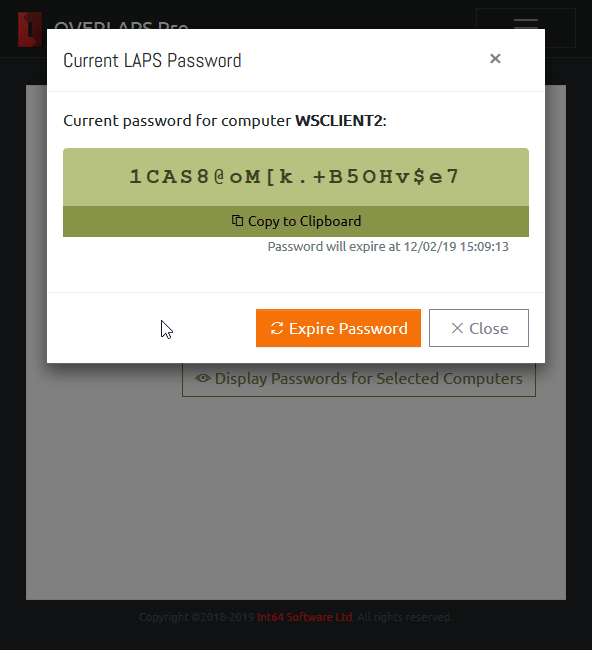
Microsoft LAPS deploys a tiny DLL to each device which is launched each time a Group Policy refresh occurs (so not a client as such, and it won’t impact on your device performance). When it detects that a password refresh is due (based on the last time the password was set and how often you specify it should occur in Group Policy), it generates a cryptographically secure random password of a defined length and complexity, applies this to the Local Administrator account and records the password in a secure field in your Active Directory schema.
You then control, through AD permissions, who can read this password value for each and every Windows device (hint: it is not recommended to use this on domain controllers of course!). This takes the onus of updating passwords regularly off of you and your Service Desk staff, guarantees a secure and completely unique password for each device.
Microsoft LAPS Pros and Cons
Pros
- Installation and setup can be done in 10 minutes
- Increased device security
- Unique admin passwords on each device
- Automatic password changes on a schedule
- Easily managed by GPO
Cons
- Requires a minor change to your AD schema
- … that’s all I’ve got!
So it is pretty obvious that if you run a decent size Active Directory managed network of Windows computers, you’re going to want to seriously think about making use of Microsoft LAPS. To further help you to take that leap, we’ve prepared a few guides to show you how easy it is to setup, see the links below.
Installing and Configuring Microsoft LAPS: A Complete Guide Part 1
Installing and Configuring Microsoft LAPS: A Complete Guide Part 2
A Look at the Microsoft LAPS Group Policy Settings
An Alternative to the Microsoft LAPS Management Tools
If you’re serious about deploying Microsoft LAPS (you should be), then you may want to consider also implementing an alternative to the rather simplistic management tools that are provided by default.
OVERLAPS is a self-hosted web UI for LAPS which provides a quick, easy to use way of retrieving and expiring LAPS managed Local Administrator passwords for your devices. You can find out more here.
Thanks
Thanks for reading, I hope it helps you in your quest for network security. If you liked this article, I’d really appreciate it if you could share it with your friends and colleagues. We’re dedicated to providing as many great resources as we can to help out our IT Service Desk friends, so you’d be helping us massively by getting the message out there.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd