
The 10 Immutable Laws of Security
Back in 2011 Microsoft published the latest version of their 10 immutable laws of security. This list provides a succinct set of ideals that every infosec or sysadmin practitioner should endeavour to follow. Sadly the article (and its predecessor) have since been removed, so I’ve decided to re-publish them with some additional information on each “law”.

1. If a bad guy can persuade you to run his program on your computer, it’s not solely your computer anymore.
The majority of successful malware attacks against individuals (whether they go on to attack the individual’s organisation or not) are a result of an individual running a program or clicking a link that was sent to them by a hacker.
In modern operating systems, it is actually quite difficult to get an executable to run without any user interaction. However attackers have had years of experience at convincing people that their program isn’t one of those nasty virus things and is instead just the screensaver that they always wanted.
Windows has mitigated this somewhat with the introduction of UAC in Vista, which can help to stop a program from automatically gaining elevated privileges. It doesn’t stop a determined victim from authorising the elevation without thinking though, and does little to protect against things like ransomware which rarely require more than basic user rights.
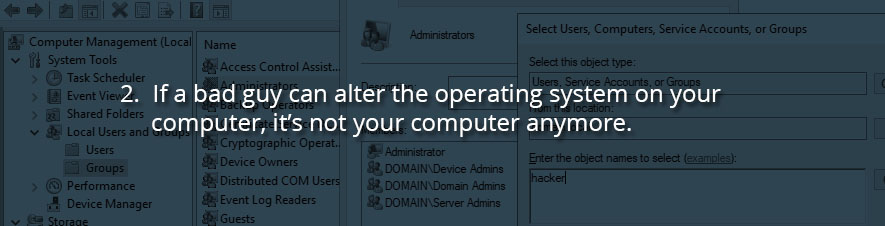
2. If a bad guy can alter the operating system on your computer, it’s not your computer anymore.
This goes without saying. From installing malware, to using your computer as the first step in a deeper intrusion into your company’s network – any ability to modify the operating system is an open door to more devious acts.

3. If a bad guy has unrestricted physical access to your computer, it’s not your computer anymore.
No matter how many layers of protection exist between a computer and the internet, they are all useless if an attacker has physical access to the computer.
While it is possible to mitigate this somewhat with strong passwords and full disk encryption, physical security should be implemented first
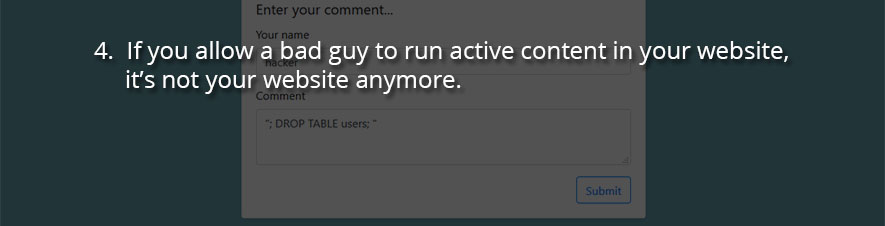
4. If you allow a bad guy to run active content in your website, it’s not your website anymore.
Moving from individual computer security to website security, this is really about preventing attacks such as Cross-Site Scripting (XSS) and SQL Injection.
If an attacker is able to run their own code (“active content”) on your website, then there are no limits to the damage they can cause. From destroying or de-facing the website itself, to capturing the credentials or payment information of other visitors.
For more information on avoiding these attacks, see part 4 of our Hardening Website Security series: Safely Handling User Input.
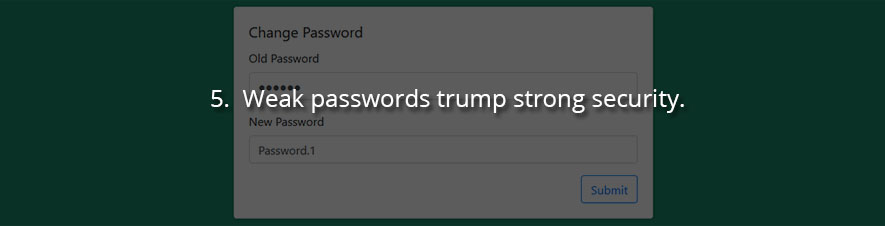
5. Weak passwords trump strong security.
You can have the best systems in the industry and the tightest security policy around, but if your Domain Administrator account’s password is “abc123” you’re going to have a bad time of it.
Minimum password lengths should be enforced, and while there are arguments against requiring certain special characters or numbers, forcing users to use them is a quick win to ensure passwords are sufficiently complicated.
So the next time you’re setting up an account, think again about using something easily guessable or brute-forcable. Particularly for privileged accounts.
Additionally, if you run an Active Directory environment, consider installing Microsoft’s free Local Administrator Password Solution (LAPS). It increases your site security by regularly randomising the passwords for the default Local Administrator account on all managed Windows computers. This can go a long way to mitigating the threat of Pass-the-Hash type attacks, for more information see our article on Why aren’t you using Microsoft LAPS yet?
If you already use LAPS, why not check out our handy web UI for it.

6. A computer is only as secure as the administrator is trustworthy.
While this completely applies to the unscrupulous types who abuse the power granted them, it is also about unnecessarily handing out permissions to those who are perhaps underskilled or lacking a full understanding of the consequences of performing actions using their elevated credentials.
An administrator account, be it for a single computer system or for the whole domain, should only be used for specific tasks that require that level of access. This is the Principle of Least Privilege.

7. Encrypted data is only as secure as its decryption key.
Decryption keys are the passwords for decoding encrypted data, and just like Law 5 a weak password trumps strong security. So it doesn’t matter if your data is encrypted using AES256, if the key used to encrypt it is “12345” (the kind of thing an idiot would have on his luggage) then it can be easily brute-forced or subjected to a dictionary attack.
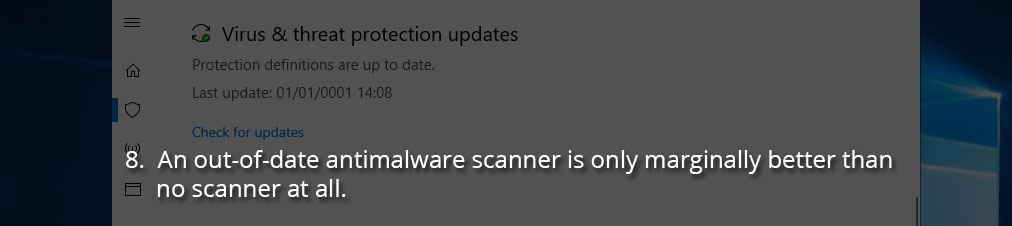
8. An out-of-date antimalware scanner is only marginally better than no scanner at all.
Computer technology is fast moving, but it’s consistently behind malware and fighting to keep up. If a virus is released which takes advantage of a new exploit, the only way you can protect against it is to make sure your antimalware scanner is kept up to date as well

9. Absolute anonymity isn’t practically achievable, online or offline.
While a decent level of anonymity can be achieved with care and a fair amount of work, absolute anonymity is largely impossible. This is how attackers can gain knowledge about your systems, your users and you; and how they can then use this information in an attack.
Acknowledging this difficulty can help you to better understand and mitigate vulnerabilities.

10. Technology is not a panacea.
Technology alone is not going to make your systems secure. To achieve the level of security needed by all modern computer driven environments, a combination of technology, solid working processes, and up-to-date training are required.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd