
Dispelling Common Myths about Microsoft LAPS
The Microsoft LAPS product (Local Administrator Password Solution) is a great free tool for securely randomising the Local Administrator password on your Active Directory computers.
Of course, being free (and, I suspect, being from Microsoft) tends to draw undue criticism which may leave some fence-sitters erring on the side of not deploying it, or worse, paying out a lot of money for third party solutions which offer little benefit over Microsoft’s own product.
Today I’m going to look at 5 of the common myths, misconceptions and unfounded fears surrounding Microsoft LAPS in the hope of convincing you that it really is worth deploying.
1. Disconnected Devices
“Systems that are not on the domain miss scheduled password changes”
If a system isn’t “on the domain” (which I take to meaning devices off-network, in the field, or taken travelling) then it won’t be updated by LAPS, this is true. But it also won’t be contactable by Group Policy, SCCM, WSUS, Remote Desktop, PowerShell, Overcee, or any other management tools. Devices used off-site are a long discussed problem for sysadmins, and subject to a more in-depth discussion that can be had here.
However, at least if you use LAPS you know that the device’s password was securely randomised before going off-site, and it will catch up with a fresh password at the earliest opportunity when reconnected.
2. Cyber-Attack Vulnerability
“Systems that don’t receive regular Administrator password changes are at risk from pass-the-hash attacks.”
This is just plain wrong.
If someone has physical access to a computer then they can, in principal, access the password hashes stored in the SAM database, this is nothing new. While it isn’t possible to fully prevent this from happening, it can be mitigated with a good security policy (full disk encryption, etc.).
However, the hash of the Local Administrator account on a Microsoft LAPS managed device is not going to help anyone in performing a pass-the-hash attack because this is one of the vulnerabilities LAPS is designed to mitigate.
A pass-the-hash attack is when someone uses a user account and its hashed password to move laterally through a network by passing this hash as proof of authentication instead of a password. As each device has its own unique Local Administrator password, this is not possible in a LAPS managed environment.
3. A Target for Hackers
“LAPS stores passwords in clear text, making it an easy target for hackers.”
Does LAPS store passwords in clear text? Yes. Is this a target for hackers? Almost certainly. Does it mean it’s vulnerable? Not so much. An important step of the proper deployment of Microsoft LAPS includes locking down the permissions on the LAPS attributes in Active Directory so that only those users deemed trustworthy can view it.
Claiming this is a target for attackers is like saying that your Domain Administrator accounts are a target for hackers: of course they are! But does that fact make them more vulnerable? No.
4. Risk to Active Directory
“Updating the AD Schema when installing LAPS could crash Active Directory.”
If this happens then you have bigger problems with your Active Directory infrastructure! To quote a slightly dated, but still relevant article:
When needed to meet your needs, extending the … Active Directory Schema is encouraged as long as you follow normal planning and test criteria.
Extending the Active Directory Schema – Microsoft Docs
5. Time Requirements and Complexity
“It’s really hard to install LAPS and it takes a lot of time.”
While developing OverLAPS, our web front-end for retrieving LAPS managed passwords, we had cause to install LAPS over 50 times on different domain configurations for testing purposes. By the end we had this process down to just a few minutes from starting the install to finishing deploying the group policy changes.
Microsoft kindly provide a collection of very simple to use LAPS PowerShell commands and Group Policy ADMX templates. These make its installation and configuration quick and painless.
If you’d like to know more about the process, check out my article “Installing and Configuring Microsoft LAPS – A Complete Guide“.
6. LAPS Management
“The LAPS Management Tools are too simple/hard to use”
Microsoft released LAPS with a PowerShell module for managing it through scripts, and a basic Windows GUI for retrieving and expiring passwords.
If you don’t have much experience with PowerShell, then the scripts may be confusing at first. On the other hand, the GUI is fairly limited in its functionality.
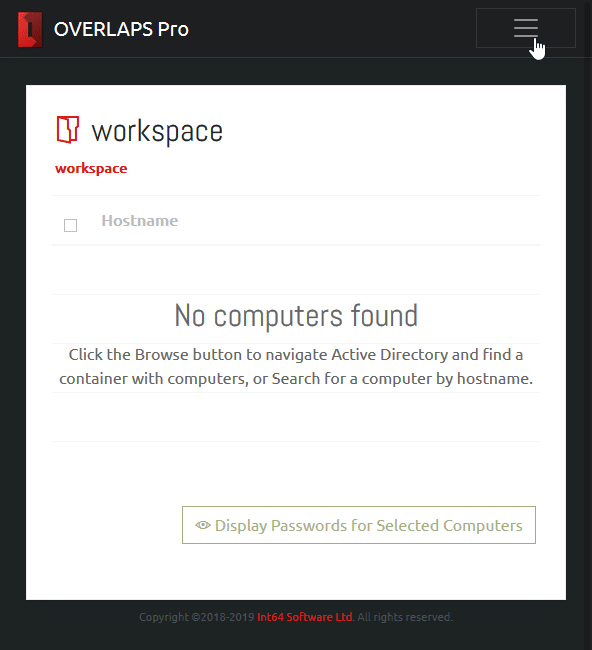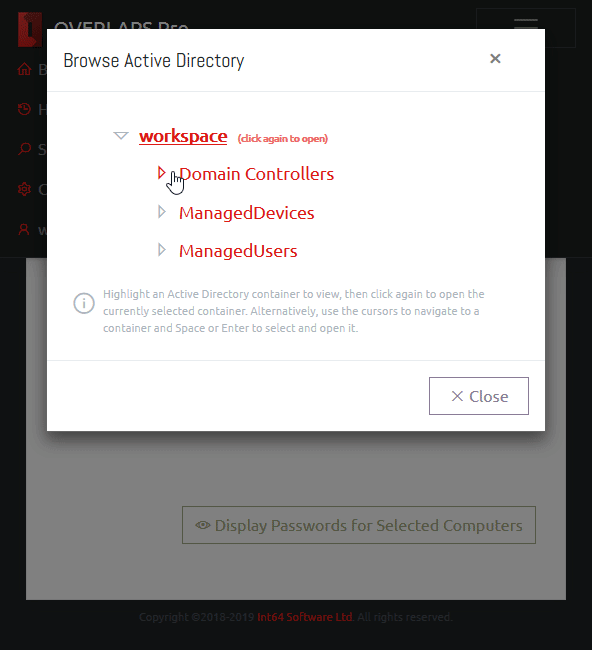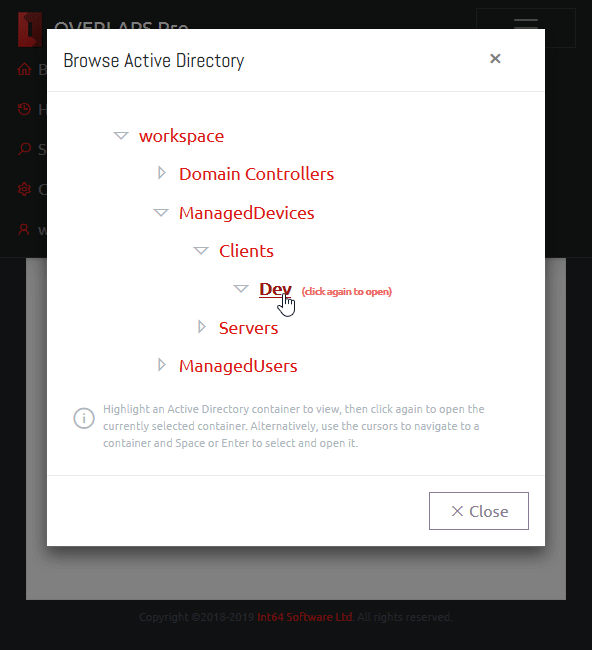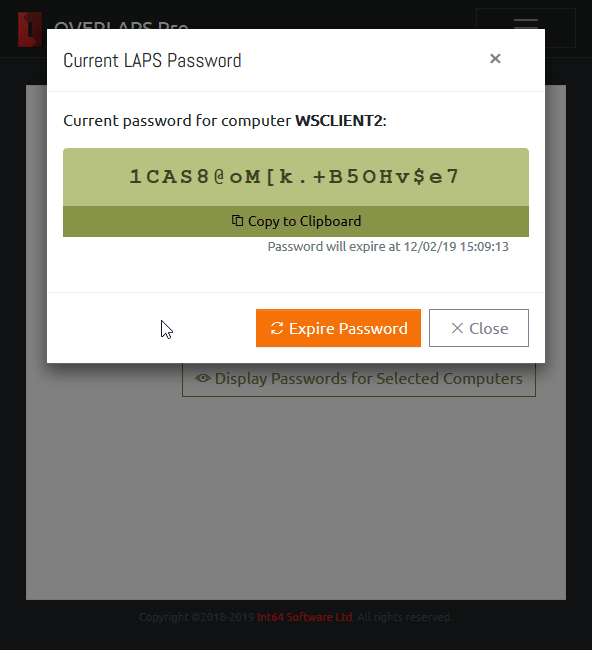
Fortunately, you don’t need to stick with just those tools though. Consider a third party UI such as my own OVERLAPS. This provides a web-based user interface with all the power of the default tools, but the added advantages that it is: easy and quick to use, and can be accessed from any device capable of browsing a website.
Conclusion
Microsoft LAPS is free, powerful and secure, so there really aren’t any good excuses for not using it. If you need more convincing, check out our article “Why aren’t you using Microsoft’s Local Administrator Password Solution (LAPS) yet?”.
Like the article? We appreciate all the help we can get in growing our readership, so please share it with your friends and colleagues.
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd