
OVERLAPS for Microsoft LAPS Update 1.3
Introduction
We are pleased to announce the release of update 1.3 for OVERLAPS, our powerful web-based UI for Microsoft’s Local Administrator Password Solution (LAPS) environments.
This is a Feature Update, bringing you a selection of new and improved things within LAPS, as well as fixing a few minor bugs. For more information, please continue reading.
Where to get it
New and Existing customers will find the 1.3 download available in their Downloads section from today. The upgrade procedure is simple and will preserve all of your existing settings.
Demo version
The demo version available here has also been updated to version 1.3 and includes all of the features and fixes shown in this article.
New Features
Feature 1: User Rate Limiting

About
You can now apply a Rate Limit to user/group accounts to specify the maximum number of password requests and/or reset operations that they can perform in a given amount of time.
This can be used to great effect to prevent excessive use of Local Administrator accounts, and for damage limitation should a user account become compromised. It could also act as a precautionary measure against users dumping all of your Local Administrator passwords in one go.
Configuration
The setting is accessed from the Config -> Users and Groups page. Select one or more accounts and click the Edit Users -> Rate Limits button.
From here, you will be presented with a new window to configure the selected users’ rate limits.
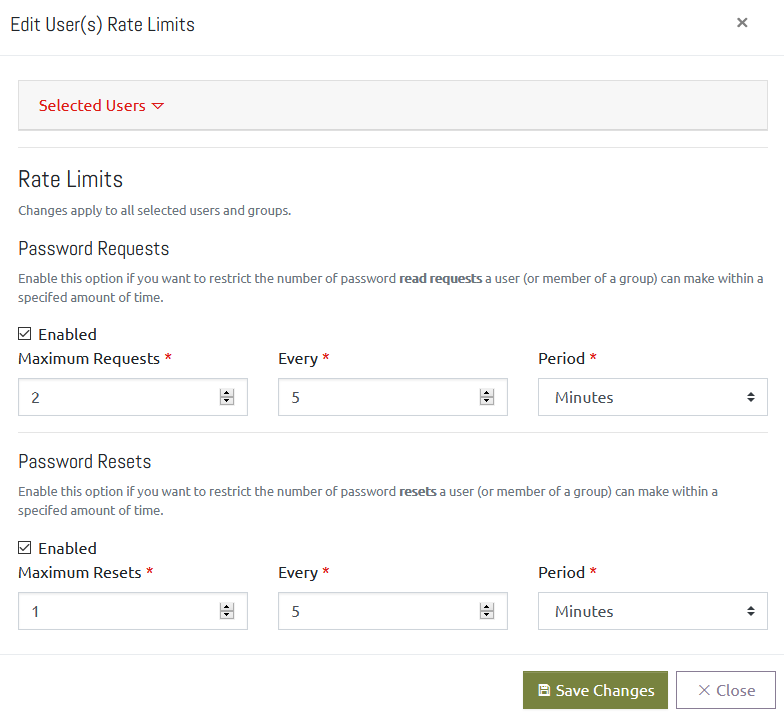
Password Request limits and Password Reset limits can be controlled independently. To set a limit:
- Click the checkbox to Enable the limit you want to impose,
- Specify a maximum number of requests (Maximum Requests/Resets) that can be performed in a specific time frame,
- Specify the time span and period that this will be monitored over,
- If the user(s) attempt more than the maximum requests in the given time period, they will be blocked.
For example, for a normal user you may want them to stay under 25 requests per day, so you would set it to – Maximum: 25, Every: 1, Period: Day.
A warning note on group memberships
In order to handle multi-group membership in an efficient and minimally complex way, there is an important point to remember. Where a user is a member of multiple groups, each with its own rate limit, OVERLAPS will select the lowest value all of the rate limit time periods AND the minimum number of requests.
This means if you have a group with a limit of 5 requests every day, and another with a limit of 25 requests every 10 minutes, a member of both groups will end up with the limit 5 requests every 10 minutes.
This is done to be in-line with least privilege best practices. If the need arises to override the rate limit a user is experiencing because of their group memberships, the correct way would be to add the user explicitly to OVERLAPS as explicit users always take priority over group memberships.
Feature 2: Separate LAPS Credentials (AFR)

About
Part of our Advanced Feature Release (AFR) program, as the result of a request we are looking at moving up our plans for increased control over security by releasing this beta feature ahead of full implementation in future patches.
In order to work seamlessly with Kerberos authentication, the OVERLAPS web service runs as either Local System (default) or Network Service on your server. This means that you need to give the same account access to the LAPS password properties in Active Directory, and this has been working well for most of our customers.
However, it has been rightly brought to our attention that in some shared server environments this may not be best practice from a security point of view as OVERLAPS may not be the only service running under that account, and you are needlessly therefore granting the same access to other services.
It has always been our plan to provide the ability to specify a different service account to use when querying LAPS, eventually we envisage this as being able to be set on a per-OU level to aid in compartmentalising your security. However, we have decided to move it up in a more generalised way, allowing our customers the option of setting a single alternative account that will be used to query LAPS.
Enabling the LAPS Credentials Feature
As this is an AFR, the option is not enabled by default and it must be enabled manually in the configuration file. When this goes to full release, it will be available by default in the program settings.
Load a text editor like Notepad (load as Admin to make sure you have write access) and load the file:
C:\ProgramData\Int64 Software Ltd\OVERLAPS\config.xmlIn you config file, locate the line “<AdvancedLAPSOptions>false</AdvancedLAPSOptions>” and change its value to “true”.
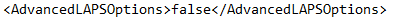
Next, restart your OVERLAPS service so that it picks up the change.
If you go to Config -> Settings now you will see a new option appear at the bottom.
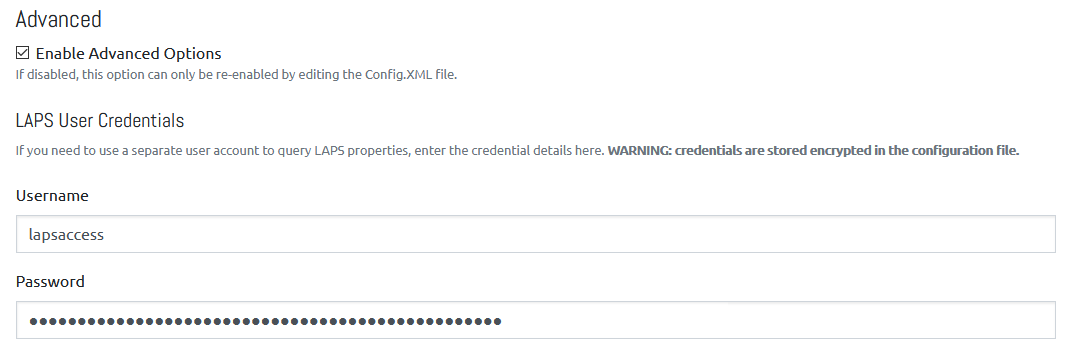
This now gives you the option to specify a username and password for OVERLAPS to use when accessing LAPS password details and performing resets.
Make sure the account you use has been pre-configured with the correct permissions by following the LAPS documentation.
Additional security information
It should be noted that the reason this feature wasn’t included in earlier versions of OVERLAPS is because it necessitates the storing of this username and password securely on the server. This is never something to be taken lightly.
To protect the credential, we take every reasonable step to securely encrypt it before storing it. We do this using the Data Protection API (DPAPI) which in turn uses the AES256 algorithm, this is also used by multiple Microsoft products, so is considered reasonably secure. However, as with any two-way encryption, a motivated attacker could still reverse it given access and time.
As way of a disclaimer, please be away that we have made all reasonable effort to protect the data on your server, but cannot be held responsible if through malice, mistake or misuse that information is obtained by third parties.
If you would like to discuss any concerns with us more fully, please feel free to contact us.
Bug Fixes

- Improved memory management in the Session Manager
- Fixed some minor display issues on niche mobile browsers
- Fixed issue in login process for users of international keyboards
Like the article? Share with your friends:
 Int64 Software Ltd
Int64 Software Ltd