22. Container Permissions
This section will show you how to configure OVERLAPS' granular container permissions.
OVERLAPS uses an ACL-like permissions system where each user or group can be granted permissions to individual containers in your Active Directory structure.
The Permissions section is split vertically into two parts: A navigation tree for finding the container you want to edit, and a list of the Users/Groups who have permission to the currently selected container.
It is important to note that any changes made here are set in OVERLAPS only. No changes are made to your Active Directory structure or permissions.
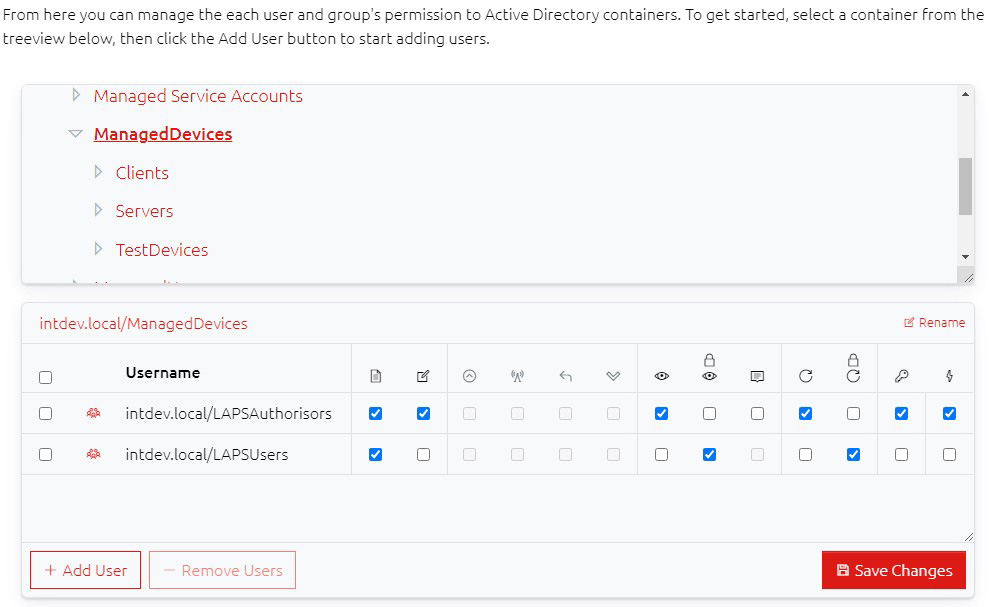
With a valid container selected, you can add or remove users using the relevant buttons, and change their permissions (see below) accordingly, but the permissions are only saved when you click the Save Changes button.
22.1 Container Permission Icons
The permissions available to each user are split into sections:
22.1.1 Computer Information Permissions
| Icon | Permission | Description |
|---|---|---|
 |
Read Computer Information | Allows the user to bring up the Computer Information window for computers in this container. Computer Information includes common attributes from Active Directory, such as Operating System information. |
 |
Write Computer Information | (Requires the Read Computer Information permission) This allows the user to edit the description of the computer from the Computer Information window. This requires OVERLAPS to have write permission to the Description property. |
22.1.2 Computer Management Tools
This list of permissions require Computer Management Tools to be enabled and configured (see Computer Management Settings for information on enabling the tools, and Computer Management Tool Permissions for information on the required permissions setup.)
| Icon | Permission | Description |
|---|---|---|
 |
Trigger Group Policy Update | Allows the user to run a Group Policy Update Computer Management Tool on the selected computers in this container. |
 |
Ping Computer | Permits the user to run an ICMP Ping on any computers selected in this container. |
 |
Restart Computer | Permits the user to remotely restart any computers in this container. |
 |
Shutdown Computer | Permits the user to remotely shutdown computers in this container. |
22.1.3 Read Password Permissions
| Icon | Permission | Description |
|---|---|---|
 |
Read Passwords | With this option checked, the user/group can read the password of any computer in this Organizational Unit. |
 |
Read Passwords with Authorisation | Alternatively, checking this option will allow the user/group to read the password of any computer in this Organizational Unit, but they will need to submit an Authorisation Request first which must be authorised by one or more nominated Authorisers. |
 |
Read Passwords with Justificaton | This option acts much like the "Read Passwords with Authorisation" setting, but instead of going through an entire authorisation process, the user must simply provide some information about why they needed access to the password, which is recorded in the History Log. |
22.1.4 Reset/Expire Password Permissions
| Icon | Permission | Description |
|---|---|---|
 |
Expire Passwords | With this option checked, the user/group can expire the password of any computer in this Organizational Unit. This will trigger the computer to reset its password when it next runs a Group Policy update. |
 |
Expire Passwords with Authorisation | As with the Read Password permissions, this also allows users to expire passwords, but will require them to submit an Authorisation Request first. |
22.1.5 Authorisation Request Authoriser Permissions
| Icon | Permission | Description |
|---|---|---|
 |
Authoriser for Normal User Requests | Checking this option nominates this user/group as an Authoriser for normal user requests. When a user who requires authorisation attempts to perform a relevant action, these users will be notified by email and must login to OVERLAPS to authorise the action. In order to have users who require authorisation to read or expire passwords, the container must also have at least one Authoriser. |
 |
Authorise Self-Service Requests | As with the regular Authoriser permissions, except this user has permission to authorise Self-Service users to read computer passwords. |
22.2 Rules for Permissions
There are a few rules to consider when settings permissions on a container:
- Users can either have "Read" permission or "Read with Authorisation" permission, you cannot check both.
- Users cannot have both "Read with Authorisation" and "Read with Justification" permissions.
- Similarly, users can only have "Expire" or "Expire with Authorisation" permissions.
- In order to add users who require authorisation, the container must have at least one nominated Authoriser user.
22.3 Permission Inheritance
To simplify the process, OVERLAPS does not support traditional permission inheritance. Instead, you can opt when saving permissions to overwrite the permissions for all child OU’s with the ones being saved for the current container.
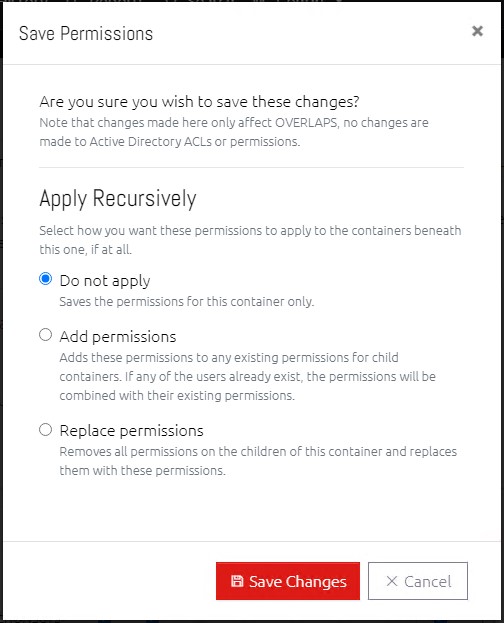
The options presented are:
The permissions will be applied to this container only.
Will add the permissions of this container to the ones below it. This merges permissions with existing users, adds users to containers that they were not previously given permission to, and will not remove any existing permissions.
This option completely replaces the permissions of child containers with the ones of this container.
22.4 Renaming a Container

Often Active Directory containers are named in a utilitarian way which may make sense from an Administration point of view but may be confusing of unclear to regular users. For this purpose, OVERLAPS supports the ability to give containers an alternative name which will show in OVERLAPS only.
To “rename” a container, select it from the tree view, then click the Rename button next to its Distinguished Name.
Renamed containers will show as blue in OVERLAPS, and hovering over it will reveal its original name.
22.5 Permissions Snapshots
You can take a quick snapshot of all of your permissions using the Permissions Snapshots feature. This will take a full copy of the permissions on every container and store it using a name of your choice. Then if you need to restore to this stage you can simply find it in the snapshot list and click the "Restore" button.
This can be useful when you are first learning to setup OVERLAPS permissions and you want to save a working state before making changes.
Note that if no permissions have been created yet then attempting to create a snapshot will show an error.
By default, OVERLAPS will also take an automatic snapshot of your permissions every night for backup purposes, which will be kept for 7 days. Both of these settings are configurable under Config -> Active Directory -> Permissions Snapshot Settings.